Group Policy Allow Software Updates
What is Group Policy Editor (GP Editor)? Group Policy Editor is a tool that helps administrators manage policy settings in Microsoft Management Console (MMC) snap- ins. It can be found on all versions of Windows Server since the release of Windows Server 2. By submitting your personal information, you agree that Tech.
Target and its partners may contact you regarding relevant content, products and special offers. You also agree that your personal information may be transferred and processed in the United States, and that you have read and agree to the Terms of Use and the Privacy Policy. Group Policy Objects (GPOs) store the policy settings set by administrators with GP Editor.
This topic for IT professionals describes the function, location, and effect of each Group Policy setting that is used to manage BitLocker Drive Encryption. Started working with New Customer since few weeks ago,running Configmgr 2012 R2 CU1,yet to upgrade to Latest CU. Powerful Point of Sale POS Software. Integration, Power, Scalability & Customization increases your business success. Issue oriented group focused on access, privacy, safety, human rights. Has links to news archives. Updated frequently.
- Last updated for Chrome 60. Both Chromium and Google Chrome support the same set of policies. Please note that this document may include policies that are targeted.
- Resolves a vulnerability in Windows. A remote code execution vulnerability exists in how Group Policy receives and applies connection data when a domain-joined system.
- Tricks, scripts and free tools for updating Group Policy Settings on remote domain computers.
- In the Windows 2000 operating system, a Group Policy Object (GPO) is a collection of settings that define what a system will look like and how it will behave for a.
This article explains how to deny logon and allow logon locally to Windows workstations.
Until the policies are applied by the system, those settings do not take effect. Extensions that work with GP Editor include administrative templates, security settings, software installation and remote installation services.
Managing the WSUS Automatic Updates Client Download, Install, and Reboot Behavior with Group Policy. Published: May 4, 2. By Bobbie Harder, Program Manager, Windows Server Update Services, Microsoft Corporation. See other Security Tip of the Month columns. Windows Server Update Services (WSUS) clients can be configured to provide update installation and reboot behavior best suited to your environment and your business needs. You can use Group Policy or Local Group Policy to modify Automatic Update configuration on your WSUS clients to determine what notification, download, install, and reboot behavior your WSUS managed clients will experience in updating from WSUS. How To Download A Book From Google Scholar Uk.
Although there are policy settings for WSUS that control additional configuration, this article focuses on configuration options that define update notification, download, installation, and post- install reboot behavior. Before discussing AU configuration options, a couple of key points should be clarified.
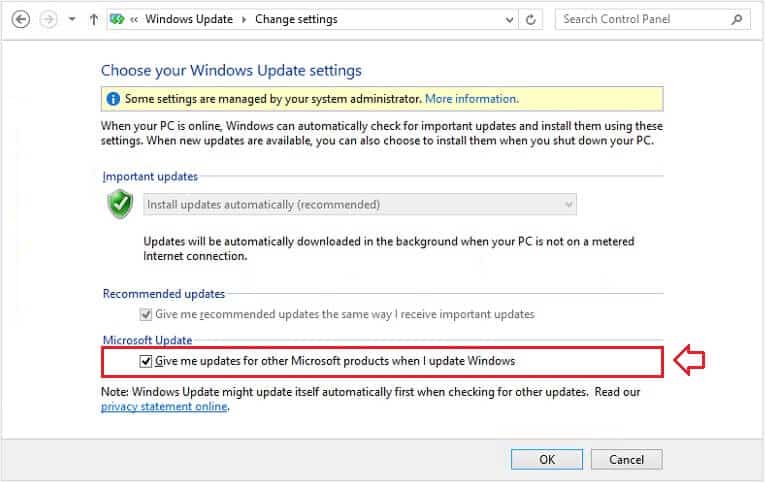
The first point is that its important to distinguish the difference between downloading and installing. After a WSUS administrator approves an update for installation for a client or a group of clients, the update must be downloaded from its mapped source (either the local WSUS server or MU). Before downloading can happen, the client must check in with the WSUS server and determine what updates have been approved for it, as well as report its current update status. By default, a client will check in with the WSUS server every 2. The AU client can be configured to notify the user before the client begins downloading, but in most cases background download of an update is set to happen without user notification because it causes no user impact. Update download happens in the background using only available bandwidth not already being consumed by the client.
For instance, if the user is doing a foreground download, browsing, or sending e- mail, downloading an update in the background will have no impact on those experiences. Once the update is on the client, depending on how the AU options are configured, the installation will occur with the appropriate administrative user logged on, as a separate and distinct action. Downloading is just getting the bits from the source to the client, while installing is the action of actually installing those bits onto the system. The AU options and policy settings discussed in this article allow WSUS administrators to customize download notification, installation, and reboot notification and experiences of their WSUS managed clients.
These two actions are interdependent for updates that require the system to be rebooted to really be installed. A security update that requires the system to be rebooted is not installed and able to protect against the intended vulnerability until such time as the system is rebooted.
Often a system or application file can only be updated when the file is not in use or locked. Additionally, a pending reboot state results in neither an updated nor a prior- to- updated state.
Further, the system is still vulnerable or unpatched while in the state of a pending reboot, and a client can no longer detect the need for future updates until the reboot has occurred. Because Automatic Updates controls the installation of updates, the installation and reboot experience for the non- local administrator versus the local administrator will vary from opaque and controlled to more transparent and flexible.
It is important when applying these policies to note the impact on and experience for both user types. In a non- Active directory environment you can use Local Group Policy or edit the registry directly. In an Active Directory environment you would use Group Policy. Its important to note that administrator- set Group Policy settings (whether set locally, in the registry, or with Group Policy) always override any machine- set or user- defined options on the client.
Whether using Group Policy or Local Group Policy, the WSUS Administrative Template file must be loaded on the system used to administer Group Policy. This template file is named Wuau. Windows XP Service Pack 2 clients. Additionally, any client machine is WSUS compatible (meaning has self updated to have the latest client version), it will also have the latest Wuau.
Inf directory. Add Standalone Snap- in dialog box. In the Group Policy Wizard, accept Local Computer, and then click Finish.- or- From Start => Run, type gpedit. Group Policy, under User Configuration, right- click Administrative Templates, click Add/Remove Templates, click wuau, click Add, click wuau. Policy Templates dialog box, and then click Open. View the console pane and the description for each associated policy as highlighted in Figure 2. Group Policy Object Editor for Local Group Policy. You can see that the Group Policy options for WSUS also include policies that configure which WSUS server clients should point to (Specify intranet Microsoft Update service location), allow the auto join of a client to a preexisting target group on the WSUS server (resulting in approvals for that target group also applying to the specified client when enabled), and allow the ability to configure the frequency of when a client checks in with a WSUS server (Automatic Update detection frequency).
From this policy, other policies can be applied to add further granularity to the behavior, but this is the base policy by which one of its configuration options will determine how AU downloads and installs. See Figure 3. This configuration option is useful in environments where maintenance windows vary and critical business demands on clients (servers or desktops) are difficult to predict, or compliance conformity requirements dictate optimal control over transferred, installed, or removed software. This option also provides the ability of the client’s Admin user to be able to select all or a subset of the approved updates, to be downloaded and/or installed on a client system.
This option will cause an icon to appear in the notification area, at the far right of the taskbar, both when the updates are ready to download and when the downloads are complete and are ready to be installed. By clicking the icon, Admin users have both the control of selecting which approved updates to download and which to install. This option permits the automatic download to occur in the background, but gives the client administrative end user the ability to select which downloaded updates to install and when to install them.
After automatic downloads are completed, an icon appears in the notification area. When users click the icon they can see which updates were downloaded and select all or some of them to install. For systems in an environment with predictable usage schedules, downloading in the background and setting a scheduled installation to occur at specific hours after core business works well for environments with static systems that are left on or in energy- saving modes. If this policy is enabled, the default time for the scheduled install is 3: 0.
A. M. If an update requires a reboot in order to complete installation, the client will automatically reboot. If an administrative user happens to be logged on during this time, they will see a restart notification and have the option to delay the reboot. Non- administrative users will see the notification (enabling them to save their work). They will not be able to delay the restart, but they can initiate the reboot. These additional policies are.
No auto- restart for scheduled Automatic Update installations. Delay Restart for scheduled installations. Re- prompt for restart with scheduled installations.
Reschedule Automatic Updates scheduled installations. Allow non- administrators to receive update notifications.